Grouper Access Management#
Gaining access to Vault is managed by the Vault Grouper updaters for each CESI unit once onboarded to vault. When a unit's namespace was originally requested, a list of group updaters was required as a part of that process. Any individual listed there will have access to Grouper to manage members but not Vault itself.
Within grouper, follow these instructions to add/remove users who need access to Vault. Follow these instructions to change who are members of the Vault grouper updaters group.
Info
Access to Vault via Grouper group membership is intended for individual, named access. Functional or departmental accounts added to the namespace's adhoc group will not be able to login to Vault. For application or machine access to Vault, one of Vault's built in authentication methods should be used (examples)
Process to Add/Remove Vault Users#
-
Login to Grouper
-
Navigate to
Root>app>HCP Vaults>ref>[unit]. If you are managing a subteam, the path will beRoot>app>HCP Vaults>ref>[unit]>[subteam]. To access a Vault subteam namespace, the user will need both a role in the [unit] & [subteam]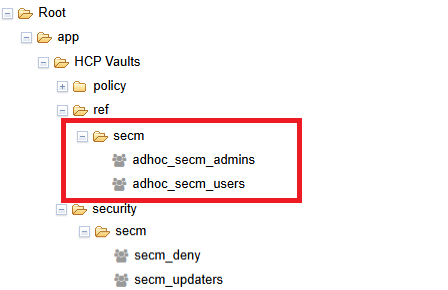
-
Open either the
adhoc_[unit]_adminsoradhoc_[unit]_usersgroup. It is up to each team to determine who will be admins versus users for their team. For a comparison of the permissions, see this articleWarning
Do not place an individual in both the
adminandusersgroups for a namespace as this will result in conflicting Vault permissions. -
To add a member, click the orange
+Add Membersbutton in the upper right corner, enter their username and click the orangeAddbutton. No start or end date is required unless your team requires it. Attestation of group members will be required every 180 days. -
To remove a member, check the checkbox next to the members name and click
Remove selected members
Process to Add/Remove Grouper Updaters#
-
Login to Grouper
-
Navigate to
Root>app>HCP Vaults>security>[unit]. If you are managing a subteam, the path will beRoot>app>HCP Vaults>security>[unit]>[subteam]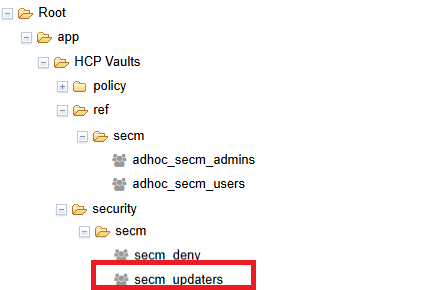
-
Open the
[unit]_updatersgroup. -
To add a member, click the orange
+Add Membersbutton in the upper right corner, enter their username and click the orangeAddbutton. No start or end date is required unless your team requires it. Attestation of group members will be required every 180 days. -
To remove a member, check the checkbox next to the members name and click
Remove selected members
Default CESI Namespace#
This structure represents the groups associated with standard CESI unit.
app
└── HCP Vaults
├── ref
│ └── [Unit Short ID]
│ ├── adhoc_[unit]_admins
│ └── adhoc_[unit]_users
└── security
└── [Unit Short ID]
├── [unit]_deny
└── [unit]_updaters
- Managers/Updaters
[unit]_updaters- These individuals have access to manage the CESI unit in grouper, without any direct Vault access. They are responsible for bi-annual attestation within Grouper and to remove team members who should no longer have access. - Admin Users
adhoc_[unit]_admins- These individuals have admin level access to the namespace in Vault. - General Users
adhoc_[unit]_users- These individuals have general level access to the namespace in Vault.
Subteam Namespaces#
This structure represents the groups associated with a CESI unit needing a Vault subteam namespace. These units will be provisioned with a shared namespace at the unit level, along with additional subteam namespaces.
Info
Certain subteam names are not available due to Vault's structure including auth, cubyhole, identity, secret, sys. CESI units will also not be able to create an secret mounts in their unit namespaces with the same name as their subteam.
app
└── HCP Vaults
├── ref
│ └── [Unit Short ID]
│ ├── adhoc_[unit]_admins
│ |── adhoc_[unit]_users
| └── [subteam]
│ ├── ad_hoc_[subteam]_admins
│ └── ad_hoc_[subteam]_users
└── security
└── [Unit Short ID]
├── [unit]_deny
|── [unit]_updaters
└── [subteam]
├── [subteam]_deny
└── [subteam]_updaters
- Managers/Updaters - unit
[unit]_updaters- These individuals have access to manage the CESI unit in grouper, without any direct Vault access. They are responsible for bi-annual attestation within Grouper and to remove team members who should no longer have access. - Managers/Updaters - subteam
[subteam]_updaters- These individuals have access to manage the CESI unit in grouper, without any direct Vault access. They are responsible for bi-annual attestation within Grouper and to remove team members who should no longer have access. - Admin Users - unit
adhoc_[unit]_admins- These individuals have admin level access to the shared unit namespace in Vault. - Admin Users - subteam
adhoc_[subteam]_admins- These individuals have admin level access to the subteam namespace in Vault. - General Users - unit
adhoc_[unit]_users- These individuals have general level access to the shared unit namespace in Vault. - General Users - subteam
adhoc_[subteam]_users- These individuals have general level access to the subteam namespace in Vault.